Find CBSE and other IT Sample Papers for Class 10 – Code 402 with Complete Solution. Prepare for IT Code 402 Class 10 by Downloading PDF Sample Papers for Pre Board or Annual Exams and Understand the complete pattern of Board Exams for all Sessions. Here, LearnCSE.in website is a one platform to get all Class 10 IT Code 402 Previous Year Question Papers and Solutions related to computer science, Information Technology or Informatic Practices.
CBSE | DEPARTMENT OF SKILL EDUCATION
INFORMATION TECHNOLOGY (SUBJECT CODE – 402)
Pre Board Sample Question Paper for Class X (Session 2023-2024) – SET 1 by KIPS Publication – Solution
Max. Time: 2 Hours
Max. Marks: 50
General Instructions:
- Please read the instructions carefully.
- This Question Paper consists of 21 questions in two sections: Section A & Section B.
- Section A has Objective type questions whereas Section B contains Subjective type questions.
- Out of the given (5 + 16 =) 21 questions, a candidate has to answer (5 + 10 =) 15 questions in the
allotted (maximum) time of 2 hours. - All questions of a particular section must be attempted in the correct order.
- SECTION A – OBJECTIVE TYPE QUESTIONS (24 MARKS):
i. This section has 05 questions.
ii. Marks allotted are mentioned against each question/part.
iii. There is no negative marking.
iv. Do as per the instructions given. - SECTION B – SUBJECTIVE TYPE QUESTIONS (26 MARKS):
i. This section has 16 questions.
ii. A candidate has to do 10 questions.
iii. Do as per the instructions given.
iv. Marks allotted are mentioned against each question/part
SECTION A: OBJECTIVE TYPE QUESTIONS
1 Answer any 4 out of the given 6 questions on Employability Skills (1X4=4 marks)
i) Feedback is an important part of the communication cycle. A good feedback is always ____ .
a. Generic
b. Specific
c. Ignored
d. Impolite
ii) ____ provide us with energy and motivation to achieve our goals.
a. Stress
b. Distress
c. Eustress
d. Depression
iii) To be a successful entrepreneur, you must be .
a. Goal – Oriented
b. Rich
c. Technology Driven
d. Visionaries
iv) What is self-motivation?
a. External pressure to perform tasks
b. The force within you that drives you to do things
c. Influence from others to achieve goals
d. The ability to avoid doing things without external influence
v) What does the “R” in SMART signify when setting goals?
a. Rigorous
b. Resourceful
c. Realistic
d. Rewarding
vi) Which of the following is a key component of sustainable development?
a. Expanding the excessive use of resources
b. Disregarding the need for resource conservation
c. Recycling and reusing waste materials
d. Ingnoring the management of renewable resources
2 Answer any 5 out of the given 6 questions (1X5=5 marks)
i) Which of the following is true about a Table of Contents?
a. Usually located at the end of a document.
b. Provides an organized list of chapters along with their page numbers.
c. Useful only for shorter documents.
d. Primarily used for fiction books.
ii) The document is creating by combining the main document with the data source fields.
a. Merged
b. Combined
c. Collated
d. Blank
iii) A file saved with the extension .ott is called a ____ .
a. Style
b. Theme
c. Template
d. Object
iv) Mail merge feature can help you in printing multiple addresses ____ on a single sheet.
a. Stickers
b. Objects
c. Labels
d. Details
v) Which category of styles will you click to set the font and size of text in a paragraph?
a. Tablet Styles
b. Paragraph Styles
c. Character Styles
d. Indent Styles
vi) ____ is a combination of title, heading, and paragraph styles.
a. Style Set
b. Font Set
c. Color Set
d. Index Set
3 Answer any 5 out of the given 6 questions (1X5=5 marks)
i) Which step should you follow before using the subtotal command?
a. Consolidate Data
b. Sort data
c. Filter data
d. both A & C
ii) Sarah, a project manager, needs to combine data from various team progress reports into a master worksheet for an overall project overview. To achieve this, she will utilize the feature of a spreadsheet known as ____.
a. Consolidate
b. Subtotal
c. Columns
d. Data Provider
iii) The ____ feature of spreadsheet enables you to keep track of the changes made by you or the other users in a spreadsheet.
a. Changes
b. Track Changes
c. Record Changes
d. Show Changes
iv) A hyperlink in a spreadsheet can be ____ .
a. Text
b. Picture
c. both a and b
d. none of these
v) ____ allows you to record a set of actions that you perform repeatedly in a spreadsheet.
a. Mail Merge
b. Review
c. Macro
d. Solver
vi. An argument can be passed through a macro function ____ .
a. By Value
b. By Reference
c. Both a and b
d. None of these
4 Answer any 5 out of the given 6 questions (1X5=5 marks)
i) In a database, the information is stored in the form of ____ :
a. Rows
b. Columns
c. Tables
d. All of the above
ii) In which type of database, can you retrieve the data from the related tables?
a. Database Management System
b. Relational Database Management System
c. Rational Database Management System
d. None of the above
iii) A table can have only one ____ key.
a. Primary
b. Secondary
c. Composite
d. Concatenation
iv) Which of the following database objects are used to retrieve data from database?
a. Queries
b. Tables
c. Reports
d. Layouts
v) The ____ SQL command is used to create a table in the database.
a. Select
b. Create table
c. Insert table
d. Add table
vi) The data type is used to store date or time or combination of date and time.
a. Date/Time
b. Calendar
c. Interval
d. Table
5 Answer any 5 out of the given 6 questions (1X5=5 marks)
i) Which of these is a psychological factor at work that can prove Hazardous?
a. Conflicts at workplace
b. Lasers
c. Presence of allergens
d. None of these
ii) Mehul is a remote worker who needs to join a virtual team meeting. He connects his laptop to a device that helps transmit digital signals over the internet. This device is referred to as a ____ .
a. Hub
b. Switch
c. Repeater
d. Modem
iii) Communication over the internet is governed by a set of rules known as ____ .
a. Topology
b. Network
c. Protocols
d. Internet
iv) The process of selling and buying products over the internet is called ____ .
a. Online Shopping
b. E- banking
c. E- reservation
d. None of these
v) The Qumana blog ____ window helps you to add a blog.
a. Helper
b. Both a and b
c. Manager
d. None of these
vi) What is the act of sending an email to a user, misleading them to believe it originates from a trusted person or organisation?
a. Phishing
b. Cracking
c. Hacking
d. Malware
SECTION B: SUBJECTIVE TYPE QUESTIONS
Answer any 3 out of the given 5 questions on Employability Skills (2X3=6 marks)
Answer each question in 20–30 words.
6. Write two ways to overcome barriers to effective communication.
Answer: Two ways to overcome barriers to effective communication are:
(i) Messages should be simple and appropriate to serve the purpose of communication.
(ii) By using the appropriate language, the sender can ensure that the receiver correctly interprets the meaning of the message being conveyed.
7 Define extrinsic motivation.
Answer: Extrinsic motivation refers to the behavior of a person that is driven by the desire to attain some sort of an external reward, including money, power, and good grades.
8 What do you understand by the term ‘Computer Maintenance’? Differentiate between hardware and software maintenance.
Answer: Computer maintenance refers to the practice of keeping computers in good condition so that they can work efficiently.
Hardware maintenance refers to the maintenance of the hardware components such as monitor, keyboard, etc., while software maintenance refers to the cleaning of the software installed in the computer.
9 What are the two types of risks usually faced by an entrepreneur?
Answer: The two types of risks usually faced by an entrepreneur are:
(i) Business Risks: These are risks associated with the day-to-day operations and decisions of the business. They can include factors like market competition, changes in consumer preferences, economic downturns, and operational challenges.
(ii) Financial Risks: These risks pertain to the financial aspects of the business, including investment decisions, funding, cash flow management, and debt obligations
10 “Natural occurrences can pose a threat to sustainability.” Explain.
Answer: Natural occurrences, such as hurricanes, earthquakes, floods, and wildfires, have the potential to cause significant damage to businesses, communities, and the environment. These events can disrupt operations, lead to physical destruction, and incur financial losses.
Answer any 4 out of the given 6 questions in 20–30 words each (2X4=8 marks)
11. What is Table of Contents? List any two characteristics of a good TOC.
Answer: A table of contents is a list of chapters at the beginning of a book. A table of content helps in navigating through a document by providing associated page numbers and direct links to various headings available on those pages.
Two characteristics of a good TOC are:
(i) It should provide a clear and concise overview of the document’s structure.
(ii) It should use descriptive headings and subheadings that accurately represent the content of each section.
12 Mention any two operations that can be performed using Macros in a spreadsheet.
Answer: Macros are used to perform different types of operations in a Spreadsheet:
(i) Formatting settings to be applied repeatedly in a spreadsheet.
(ii) Sorting Data.
(iii) Applying mathematical functions/formulas.
13 Sharing a spreadsheet is useful. Why?
Answer: Sharing a spreadsheet is useful because:
(i) It allows multiple users to work on the same document simultaneously, making it easier to collaborate on projects.
(ii) It helps in tracking changes, so we can revert to previous versions if needed.
14 Differentiate between DML and DDL.
| DML (Data Manipulation Language) | DDL (Data Definition Language) |
|---|---|
| DML stands for data manipulation language that deals with data manipulation operations within a database. | DDL stands for Data Definition Language that deals with defining and managing the structure of the database objects. |
| It includes commands like INSERT, UPDATE, and DELETE. | It includes commands like CREATE, ALTER, and DROP. |
15 Why do you need to back-up your data?
Answer: Backing up data ensures that we can recover our important files and information in case of natural disasters like floods, fires, or earthquakes. It provides a historical record of our files, allowing us to revert to earlier versions if needed.
16 Mention two preventive measures that can be taken to prevent accidents at the workplace.
Answer: Two preventive measures that can be taken to prevent accidents at the workplace are:
(i) Provide comprehensive training to employees about workplace safety, including proper handling of equipment, emergency procedures, and awareness of potential hazards.
(ii) Conduct routine inspections of the workplace to identify and address potential safety hazards. This includes checking equipment, ensuring proper signage, and maintaining a clean and organized workspace.
Answer any 3 out of the given 5 questions in 50–80 words each (4X3=12 marks)
17 List the different styles categories available in document.
Answer: The different style categories available in document are:
(i) Paragraph Styles: It defines the formatting attributes for entire paragraphs of text. This includes settings such as font, size, indentation, line spacing, and alignment. Applying a paragraph style will automatically apply these attributes to the selected paragraph(s).
(ii) Character Styles: This allows us to define specific formatting attributes for individual characters or words within a paragraph. This can include changes in font, size, color, and other characteristics.
(iii) Page Styles: This controls the layout and formatting of entire pages in a document. They include settings for page size, orientation, margins, headers, footers, and background. Page styles are useful for creating documents with different layouts (e.g., portrait vs. landscape) or for customizing headers and footers.
(iv) Frame Styles: These are used to format text frames, which are containers that hold text or graphics. Frame styles define attributes such as borders, backgrounds, padding, and text flow within the frame.
(v) List Styles: This defines the formatting of numbered or bulleted lists in a document. This includes settings for the type of numbering or bullet points, indentation, and spacing between items.
(vi) Cell Styles: These are used to format individual cells or groups of cells. This includes settings for font, borders, background color, alignment, and more.
18 What is a solver? How is it different from Goal Seek?}
Answer: A solver is a mathematical tool or algorithm used in spreadsheet software to find an optimal solution to a problem, typically by adjusting certain variables while considering a set of constraints. Solvers can be used to maximize or minimize a target value, subject to specific constraints.
Goal Seek, on the other hand, is a specific feature in spreadsheet software that allows you to set a target value for a particular cell and then find the input value needed to achieve that target. It is primarily used for finding a specific solution to a problem, rather than optimizing for the best outcome.
Using Goal Seek: Usually, you run a formula to calculate a result based upon existing values. By contrast, using the Goal Seek option, you can discover what values will produce the result that you want.
Using the Solver: Solver is a more elaborate form of Goal Seek. The difference is that the Solver deals with equations with multiple unknown variables. It is specifically designed to minimize or maximize the result according to a set of rules that you define. Each of these rules sets up whether an argument in the formula should be greater than, lesser than, or equal to the value you enter.
19 What precautions must be taken to improve the internet security?
Answer: Some precautions we can take to improve the internet security are:
(i) Use strong and unique passwords that include a mix of upper and lower-case letters, numbers, and special characters.
(ii) Regularly update our operating system, software applications, and antivirus/anti-malware programs to patch security vulnerabilities.
(iii) Avoid entering sensitive information on websites that do not have a secure connection (look for “https://” in the URL and a padlock icon in the browser).
(iv) Avoid clicking on suspicious links or downloading attachments from unknown or unexpected sources. Be wary of phishing emails.
(v) Install a reliable antivirus and anti-malware program to detect and protect against viruses, malware, and other online threats.
(vi) Perform regular backups of important files and data.
(vii) Use a firewall to monitor incoming and outgoing network traffic.
20 Sudheer is not clear about the use of a database. Explain to him the following to give him a better understanding of the DBMS concepts.
a. Describe any four advantages of DBMS.
Answer: Advantages of DBMS:
(i) Improved data sharing: Users of a database can share information among themselves.
(ii) Improved data security: DBMS provides security to sensitive data by performing authorization checks and enforcing selective access to the users.
(iii) Better data integration: Data integrity means maintaining and assuring the accuracy and consistency of data.
(iv) Reduces data redundancy: All the information is kept in only one place, and no need to maintain a separate copy of the same data over and over again, this ensures there is no duplication and redundancy.
b. State the relationship and difference between a primary and foreign key.
Answer: A primary key is used to ensure that the value in the particular column is unique. The foreign key provides the link between two tables. A foreign key is a column or a set of columns in one table that references the primary key columns in another table.
Difference:
• A table allows only one primary key but can allow more than one foreign key.
• The primary key doesn’t allow null values and cannot be deleted. Foreign key accepts multiple null values and can be deleted.
21 Consider the following table name Employee and write the queries for the following: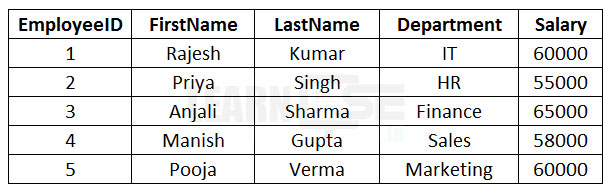
i. Write an SQL command to display the employees in descending order of their salary.
Answer: SELECT * FROM Employee ORDER BY Salary DESC;
ii. Write a query to display the details of employees who belong to the ‘HR’ department.
Answer: SELECT * FROM Employee WHERE Department = 'HR';
iii. Write an SQL query to display the details of the employees whose salary falls within the range of 50000 and 60000.
Answer: SELECT * FROM Employee WHERE Salary BETWEEN 50000 AND 60000;
iv. Write a query to delete the employee with EmployeeID 3 from the table.
Answer: DELETE FROM Employee WHERE EmployeeID = 3;

2 thoughts on “CBSE Class 10 IT Code 402 Pre Board Sample Question Paper 2024 – Solution”